Demystifying VPN
- 27 / Oct / 2020
- By: Sarath G
- Comments: 2

VPN (Virtual Private Network) is a common term which have been heard by a lot of internet users. But have you ever thought about the real scope of VPNs?.
If the answer is YES, it’s great you are a real researcher.
If the answer is NO, let us explore this article.
When we hear about VPN the first thing that comes to our mind is “Blocked websites and IP spoofing”. But it’s not all about those.
Actually the “VPNs are creating a private network in public network.” , Confusing? let us discuss about private and public networks.
Public Network
Public network can be defined as the INTERNET. it is the network where all of us have access
Private Network
Private networks can be defined as our local area connections. It is the network where only few are allowed to access.
Why should we use the VPN?
The main problem of public network is the security, as I have mentioned above the public network can be accessed by anyone which means an attacker is also able to connect to the public network. If we need to sent something to a remote person we need to use the public network but we can’t share sensitive files or information using public network because the attackers may be able to capture those information. So that what we can do to share a sensitive file to a remote person securely?
Yes your guess is right.. The VPN stands as the solution for this problem.
How it works ?
Before moving on please keep the word “Virtual Private Network” in your mind. As I have said earlier the VPNs are creating a private network in public network, which means;
When we are using a VPN connection in our organization it will create another network which can be accessed by only few peoples (Private Network) and those peoples with authorization can access this network from anywhere in the world (Public Network) which means it is creating a virtual private network in the internet. Hope you understood the idea about the VPN.
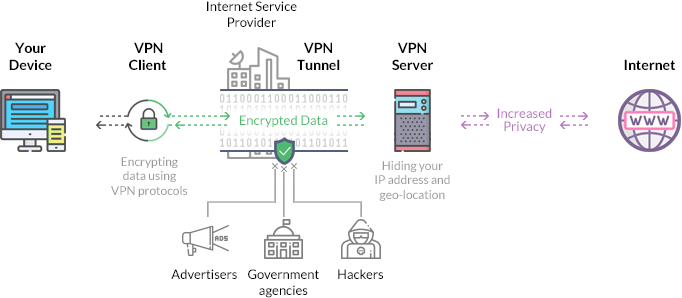
How VPN is securing our communication?
When we are connected to a VPN it will create a tunnel for those authorized users. In which the VPN will isolate those users from the public network . This virtually created network can be accessed by only authorized users which will make the connection more secure also VPN have a special character which will help the user to make the communication more secure, In VPN if it detects someone is trying to penetrate the tunnel it will shutdown itself and will create a new one, which will make the participants of VPN more secure.
Two Types of VPN
(i) Remote Access VPN
(ii) Site-to-site VPN
Remote Access VPN
Remote access VPN allows the authorized users to connect into the private network and access it’s resources remotely. This one is mostly used by the home users and companies.
eg : A corporate employee, while traveling, uses a VPN to connect to his/her company’s private network and remotely access files and resources on the private network.
Site -to-site VPN
Site-to-site VPN are used by corporate(companies, with offices in different geographical locations), The site-to-site VPN is also know as router-to-router VPN. This kind of VPN enable the users to access his/her network in one office location while on another office location. When multiple offices of same company is connected in this VPN it is called as intranet based VPN and when companies use this VPN to connect to the office of another company it is called as extranet VPN
Protocols used in VPN
There are five types of protocols used in Virtual Private Network. They are as follows;
IPSec , L2TP , PPTP , SSL&TLS , SSH
IPSec
Internet Protocol Security or IPSec is used to secure Internet communication across an IP network. IPSec secures Internet Protocol communication by authenticating the session and encrypts each data packet during the connection. There are two types of IPSec operates in two modes, they are as follows;
(i) Transport Mode
(ii) Tunneling Mode
Transport Mode
In transport mode the IPSec encrypts the message (Payload) in the data packet.
Tunneling Mode
In tunneling mode the IPSec encrypts the entire data packet.
The IPSec protocol can be used along with other protocols for an additional security of the communication.
L2TP
Layer 2 Tunneling Protocol (L2TP) is a tunneling protocol which is used along with other VPN communication protocol like IPSec to create highly secure VPN connection. When the L2TP is combined with IPSec to create a VPN communication the L2TP will create the VPN tunnel for communication and the IPSec encrypts each and every packets which are transferred through that tunnel.
PPTP
Point-to-Point Tunneling Protocol or PPTP creates a tunnel and encapsulates the data packet in that communication. Point-to-Point Protocol Tunneling Protocol (PPTP) uses Point-to-Point Protocol (PPP) to encrypt data packet in the communication.
SSL & TLS
SSL (Secure Socket Layer) and TLS ( Transport Layer Security ) creates a VPN connection where the web browser acts as the client. SSL and TLS protocol are mainly used in online shopping websites. Web browsers switch to SSL with ease and with almost no action required from the user , since web browsers come integrated with SSL and TLS. The SSL connections have https in the beginning of the URL instead of http.
SSH
Secure Shell or SSH creates the VPN tunnel through which data transfer happens and also ensure that the tunnel is encrypted. SSH connection is established by the client and the data is transferred from the local port of the client machine to the remote machine using the encrypted tunnel.
That’s all about the Virtual Private Network. In this article we have discussed about the VPN , Why should we use it , How the VPN works, Types of VPN , Protocols used in VPN.